Zte Zxdsl 931Wii Firmware Latest Version
- Zte Zxdsl 931wii Firmware Latest Version Update
- Zte Zxdsl 931wii Firmware Latest Version Download
- Zte Zxdsl 931Wii Firmware Latest Version
The BT modem is a Huawei HG612. Like the ZTE ZxDSL-931wii, the Huawei also has a Broadcom 6368 processor. This is a dual core MIPS32. I was just looking at the firmware images supplied by ZTE Finland, and they are in the standard Broadcom BC310+ format. As such it is possible to extract the bootloader, the kernel and the root file system. Zte zxdsl 831 you current version firmware. Producing popular ebook you have a new router. Click allow and subscribe to notifications for the latest news and updates. Overview of device information this information reflects the current status of your dsl router. User's manual zte zxdsl 831 series for the operator.
Zte Zxdsl 931vii Firmware Stock ROM firmware
The download APK for Zte Zxdsl 931vii Firmware on a android version: Nougat/Q/Pie/Lollipop/Lollipop/Marshmallow/KitKat/Oreo Firmware free download.
.Select your android version:
Android Gingerbread 2.3.3 - 2.3.7 2010 year
- App Name: FirmwareAndroid_2.7.APK
- Languages: English , Multi-language
- File Size: 9.1 MB
- Last update: 17 April 2021
- File Type: application/vnd.android.package-archive
- Version: 2.7
- Downloads: 23 947
Download Now
Android Ice Cream Sandwich 4.0.3 - 4.0.4 2011 year
- App Name: FirmwareAndroid_8.5.APK
- Languages: English , Multi-language
- File Size: 4.37 MB
- Last update: 11 April 2021
- File Type: application/vnd.android.package-archive
- Version: 8.5
- Downloads: 85 050
Download Now
Android Jelly Bean 4.1.x 2012 year
- App Name: FirmwareAndroid_8.9.APK
- Languages: English , Multi-language
- File Size: 5.67 MB
- Last update: 19 May 2021
- File Type: application/vnd.android.package-archive
- Version: 8.9
- Downloads: 13 343
Download Now
Android Jelly Bean 4.2.x 2012 year
- App Name: FirmwareAndroid_2.4.APK
- Languages: English , Multi-language
- File Size: 2.66 MB
- Last update: 03 June 2021
- File Type: application/vnd.android.package-archive
- Version: 2.4
- Downloads: 98 943
Download Now

Android Jelly Bean 4.3 2013 year
- App Name: FirmwareAndroid_5.6.APK
- Languages: English , Multi-language
- File Size: 6.18 MB
- Last update: 08 July 2021
- File Type: application/vnd.android.package-archive
- Version: 5.6
- Downloads: 25 428
Download Now
Android KitKat 4.4 2013 year
- App Name: FirmwareAndroid_8.4.APK
- Languages: English , Multi-language
- File Size: 4.42 MB
- Last update: 06 May 2021
- File Type: application/vnd.android.package-archive
- Version: 8.4
- Downloads: 72 310
Download Now
Android Lollipop 5.0 2014 year
- App Name: FirmwareAndroid_3.3.APK
- Languages: English , Multi-language
- File Size: 4.26 MB
- Last update: 30 April 2021
- File Type: application/vnd.android.package-archive
- Version: 3.3
- Downloads: 12 591
Download Now
Android Lollipop 5.1 2015 year
- App Name: FirmwareAndroid_5.2.APK
- Languages: English , Multi-language
- File Size: 5.52 MB
- Last update: 20 June 2021
- File Type: application/vnd.android.package-archive
- Version: 5.2
- Downloads: 79 205
Download Now
Android Marshmallow 6.0 2015 year
- App Name: FirmwareAndroid_7.1.APK
- Languages: English , Multi-language
- File Size: 5.35 MB
- Last update: 25 April 2021
- File Type: application/vnd.android.package-archive
- Version: 7.1
- Downloads: 48 563
Download Now
Android Nougat 7.0 2016 year
- App Name: FirmwareAndroid_4.2.APK
- Languages: English , Multi-language
- File Size: 3.14 MB
- Last update: 17 March 2021
- File Type: application/vnd.android.package-archive
- Version: 4.2
- Downloads: 82 626
Download Now
Android Nougat 7.1 2016 year
- App Name: FirmwareAndroid_8.8.APK
- Languages: English , Multi-language
- File Size: 2.35 MB
- Last update: 07 June 2021
- File Type: application/vnd.android.package-archive
- Version: 8.8
- Downloads: 77 695
Download Now
Android Oreo 8.0 2017 year
- App Name: FirmwareAndroid_9.8.APK
- Languages: English , Multi-language
- File Size: 5.81 MB
- Last update: 19 June 2021
- File Type: application/vnd.android.package-archive
- Version: 9.8
- Downloads: 54 322
Download Now
Android Oreo 8.1 2017 year
- App Name: FirmwareAndroid_4.APK
- Languages: English , Multi-language
- File Size: 7.36 MB
- Last update: 23 March 2021
- File Type: application/vnd.android.package-archive
- Version: 4
- Downloads: 72 310
Download Now
Android Pie 9.0 2018 year
- App Name: FirmwareAndroid_9.3.APK
- Languages: English , Multi-language
- File Size: 8.92 MB
- Last update: 08 March 2021
- File Type: application/vnd.android.package-archive
- Version: 9.3
- Downloads: 85 085
Download Now
Android Q 10.0 2019 year
- App Name: FirmwareAndroid_6.8.APK
- Languages: English , Multi-language
- File Size: 3.71 MB
- Last update: 11 July 2021
- File Type: application/vnd.android.package-archive
- Version: 6.8
- Downloads: 14 182
Download Now
Android 11 2020 year
- App Name: FirmwareAndroid_9.1.APK
- Languages: English , Multi-language
- File Size: 8.6 MB
- Last update: 06 July 2021
- File Type: application/vnd.android.package-archive
- Version: 9.1
- Downloads: 21 875
Download Now
Android 12 2021 year
- App Name: FirmwareAndroid_3.APK
- Languages: English , Multi-language
- File Size: 3.62 MB
- Last update: 10 March 2021
- File Type: application/vnd.android.package-archive
- Version: 3
- Downloads: 21 068
Download Now
Android All - universal version
- App Name: FirmwareAndroid_9.6.APK
- Languages: English , Multi-language
- File Size: 6.61 MB
- Last update: 12 March 2021
- File Type: application/vnd.android.package-archive
- Version: 9.6
- Downloads: 43 052
Download Now
Watch YouTube video - How to update Stock ROM firmware in Zte Zxdsl 931vii Firmware?
How to install APK file?
Full guide how to install apk file on android device.

All rights reserved. Unauthorized reproduction, in whole or in part is strictly prohibited.
Latest Comments

This app has a clean design and is easy to use.
Totally awesome. Thanks! Firmware APK 2021 Free August - Zxdsl Firmware Free Download [newest Version] 931vii Updated Zte
The application used to be great
I really like this! Zte [newest APK 931vii Download Updated 2021
It's a great app and always a work in progress. The developer is very responsive and open to suggestions and feedback which is rare these days.
Excellence at it's pure form Version] Free Download Updated Zxdsl August Firmware Firmware Free APK -
Outstanding
It works pretty good
Zte Zxdsl 931wii Firmware Latest Version Update
A very good application
This app works great with my Isy. I highly recommend trying it out you won't be dissatisfied
POPULAR TODAY
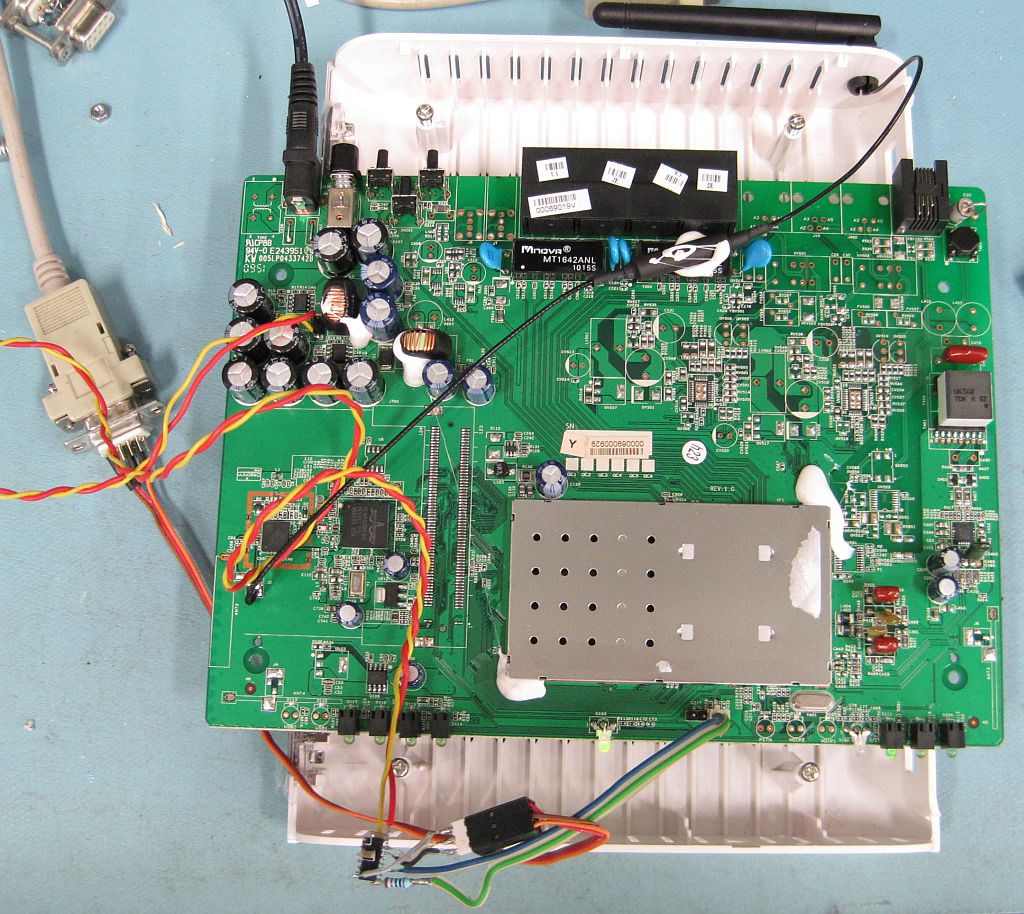
Quite some time ago (late 2011) I got sufficiently bored to poke and prod the firmware of a ZTE ZXDSL 931WIIA brand VDSL2 device, primarily to find out if it had a usable telnet interface and/or a convenient way to run arbitrary code. I always meant to write up a description of what was hiding under this particular rock, but never got around to. Well, here we (belatedly) are.
Disclaimers: Most things in the following are likely to be — more or less — particular to the exact model and firmware version (ZXDSL931WIIA_ElisaV2.8.2a_Z40_FI) I have. The model is probably discontinued by now, but perhaps the illustrated principles may be helpful for someone. If you still have one, don't try any of this at home if you're very attached to the device. Finally, the approach taken is a very 'manual' one (GNU binutils, dd, etc.), and more intelligent tools could well make it simpler.
Zte Zxdsl 931wii Firmware Latest Version Download
tl;dr? There is a telnet interface (in this version), with hardcoded ZTE 'debugging' username:password pairs, allowing for full root shell access.
Getting Started
Zte Zxdsl 931Wii Firmware Latest Version
Out of the box, my device answered with a HTTP admin interface at port 80, and a telnet login prompt at port 23. However, the user names and passwords for the web admin interface did not work at all for the telnet login, which was a shame. The scant documentation available for the device did not mention the telnet side at all. The most straight-forward way to find out what the telnet login prompt was expecting seemed to be to obtain a copy of the firmware running on the device, and take look around.
It would have been, of course, possible to start poking around looking for potential holes in the HTTP interface 'empirically'. Clearly, though, having access to a copy of the firmware on a real computer would make things significantly easier. However, the ISP who provided the device (Saunalahti/Elisa) had decided not to provide any firmware upgrade images available for downloading, opting instead to unilaterally push upgrades over a TR-069 remote management session.
After some searching, I located an image of a different firmware version (listed as V1.5.0c_Z31_FI2) from the (now defunct) ztefinland.com website. Based on circumstantial evidence, this seemed to be a version used by a different ISP (Sonera). Under the assumption that many bugs/misfeatures would be common to all versions, starting from this file felt like a reasonable plan.
Looking For a Hole
The firmware upgrade file format is likely to be common to several devices, but it was also mostly self-evident.
It seemed quite safe to say the file was a combination of some headers, followed by an executable image of some kind, followed by a squashfs-lzma filesystem image (the magic string of which is 'qshs'). For the record, squashfs-lzma was a (now discontinued) set of patches to the squashfs file system to make it support the LZMA compression algorithm; more recent versions of squashfs include this feature natively. A short dd if=firmware.img of=squashfs.img bs=56680 skip=1 (quick tip: modern GNU dd has a useful iflag=skip_bytes option) and unsquashfs later, I had an obvious root file system to play around in.
In order to dump the root filesystem of the firmware actually in my unit, any method for running arbitrary shell commands would do. A shell injection vulnerability in the HTTP admin interface seemed like a logical place to start from. Fortunately (or is that unfortunately?), it did not take long to find one.
I've misplaced my notes on the details of this middle part, so the following is an approximate overview of what happened. The (later) analysis for the login prompt of the telnet interface will be carried out in more detail, however.
In general, good candidates for shell injection vulnerabilities are any features involving operations that need root privileges. The HTTP interface has a page for configuring static routing table entries, which sounded like a promising candidate. After disassembling the httpd and following its references to lib/private/libcms_core.so, it became clear that to add a new static route, the box executed something to the tune of system('route add -net N netmask M gw G dev D');. The parameters N, M and G were verified to be IP addresses, but D was passed as-is, presumably because it was selected using a drop-down box in the HTTP interface.
As closely as I can recall, I plugged in a USB stick with a built-for-MIPS BusyBox on it (the version on the device was too stripped down), and ran a suitable route-adding command to get a remote shell open over netcat. After that, it was a simple matter of tar ... | nc to extract the contents of the existing firmware.
Telnet Login
Theoretically speaking, the task (getting access over telnet, running arbitrary code) was in a sense accomplished at this point. However, the shell injection method was both cumbersome and inelegant, especially given that there was a perfectly good telnet interface just waiting for acceptable login credentials. It was clearly time to go look at still more MIPS assembly.
The message given as the telnet login prompt was found only in the file lib/private/libcms_cli.so. As an educated guess, that seemed likely to contain the code for the command-line interface. Further, bin/telnetd linked against the library, and used symbols such as cmsCli_printWelcomeBanner and cmsCli_authenticate from it. Going purely on the name, the last sounded especially relevant.
$ mips-elf-readelf -Da lib/private/libcms_cli.so
Based on the above, the code for cmsCli_authenticate can be found by extracting 872 bytes at offset 0x2c68 in the file. That can be done with e.g. dd if=lib/private/libcms_cli.so of=auth.bin bs=1 skip=11368 count=872; mips-elf-objdump --architecture=mips:isa32 -EB -b binary -D auth.bin --adjust-vma=0x2c68. The full disassembly, along with the comments I wrote for myself, can be found in cmsCli_authenticate.txt. To make a long story short, however, it is essentially equivalent to the following C code. (Some minor details have been omitted.)
In other words, regardless of what user accounts have been configured in the HTTP interface, the telnet login prompt accepts either root:public or ztedebug:ztedebug (and nothing else) as valid credentials.
Further Discussion
The telnet interface is not very polished, but it allows you to drop into a (root) shell with the sh command, which is nice. There is no reasonable way (that I know of) to register code to be executed automatically at startup, which is less nice, as it means all customizations that cannot be performed by setting NVRAM variables are lost on reboot. It is quite possible that some shell injection trick could be used by setting one of the NVRAM variables, but I have not investigated this further.
As far as I have been able to determine, both the telnet and HTTP interfaces are only visible to the physical Ethernet and local wifi interfaces, not the DSL/WAN side. So you do not have to worry about random people from the Internet logging in as ztedebug. On the other hand, if you have untrusted local clients in the network, you do have to worry about them.
There are a number of other curiosities in the firmware (for example, a rather bizarre way of doing DNS for clients behind a NAT), but those fall outside the scope of this text.
I've since heard anecdotally that there exists a newer Elisa-branded firmware version (ZXDSL931WIIA_ElisaV2.8.3_Z40_FI) that possibly disables the telnet interface entirely.